Google: Hackers using Google Collection for phishing attacks: Report – Times of India

How hackers are using email to spread phishing attacks
The report notes that the first email received by the victims arrives in typical fashion, via a notification directly from Google. This is because the hacker shared the collection with the end user. The email comes from a [email protected] address. That address is legitimate and can be recognised by hackers and end-users alike. Users may also tend to click on the link as hovering over the URL will show a legitimate Googe link. Moreover, the emails are also redirecting users to a legitimate Google page.
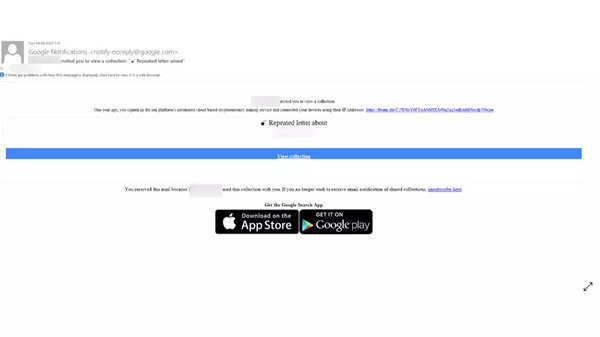
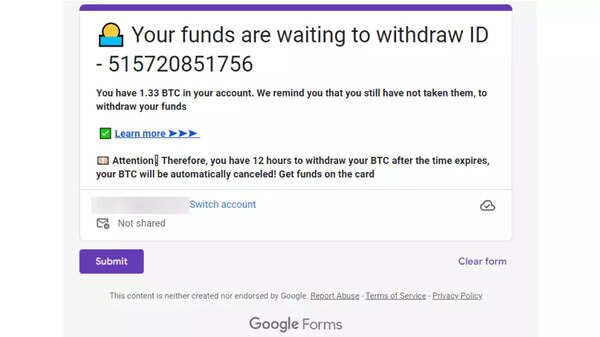
Google Collections work with several different card-like figures. Users can also link to images, webpages, etc within that collection. However, clicking on the card is showing a suspicious link and message. The hackers want their victims to enter this link which looks like a Google form. Clicking this will redirect users to a fake cryptocurrency site, which will eventually steal money.
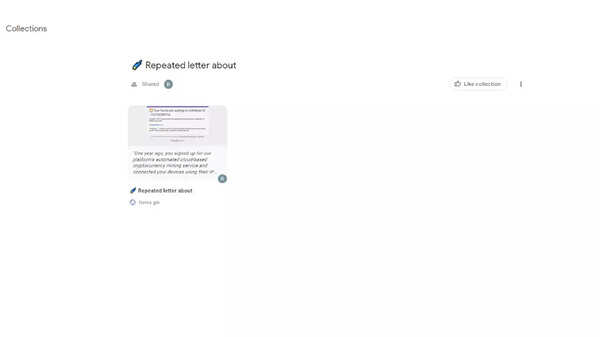
How to identify such an email
As shown in the images above, the bottom of the Google page tells an important distinction: “This content is neither created nor endorsed by Google.” Like many other sites, Google also allows users to put any content on their page and hackers are abusing this privilege by placing illegitimate, malicious sites.
The report also notes that hackers are nesting the malicious links to ensure that their payloads get to their target. For this, attackers are hiding these links in the third part. Seeing the Google links user may start trusting the links and hackers are leveraging this common confidence among users.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
