Singapore sees spikes in ransomware, botnet attacks | ZDNet
(Source: Cyber Security Agency of Singapore)

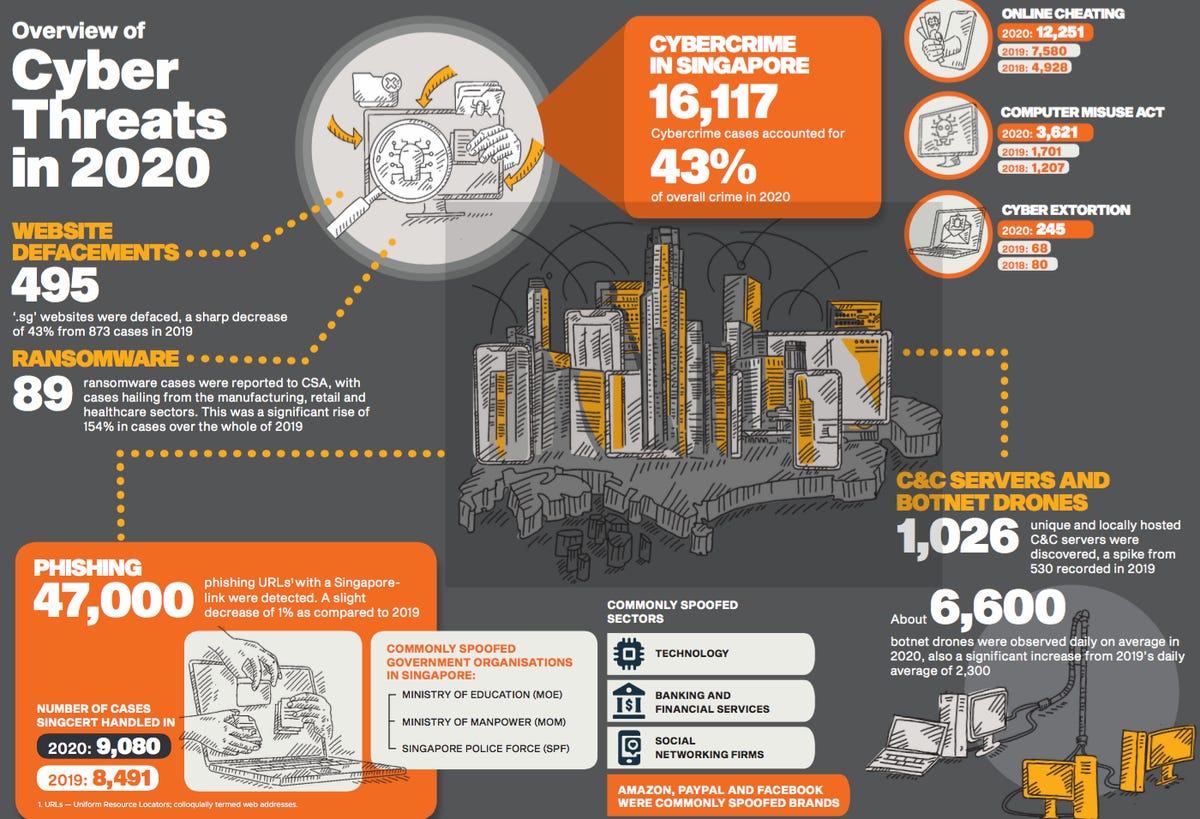
The number of reported cybercrime cases accounted for almost half of total crimes in Singapore last year, where both ransomware and botnet attacks saw significant spikes. The city-state is anticipating intensifying threats from ransomware as well as malicious attacks targeting remote workers and supply chains.
The Singapore Computer Emergency Response Team (SingCERT) last year handled 9,080 cases, up from 8,491 the year before and 4,977 in 2018, according to the latest Singapore Cyber Landscape report released Thursday by Cyber Security Agency of Singapore (CSA). The government agency noted that last year saw marked increases in ransomware, online scams, ad COVID-19 phishing activities.
In particular, the number of reported ransomware attacks saw a significant spike of 154% in 2020, with 89 incidents, compared to 35 in 2019. These mostly affected small and midsize businesses (SMBs) in various sectors including manufacturing, retail, and healthcare.
In one such incident in August 2020, an F&B business found its servers and devices infected with NetWalker, with a ransom note directing the company to a webpage on the Dark Web to view the ransom demands. None of the F&B company’s data could be recovered as it also stored its backups on the affected servers and it had to rebuild its IT system from scratch.
CSA attributed the increase in ransomware cases in Singapore to the global ransomware outbreak, where such attacks moved from being indiscriminate and opportunistic in nature to more targeted “Big Game Hunting”. Cybercriminals also shifted towards ransomware-as-a-service and “leak and shame” tactics, the agency said.
It noted that the number of malicious command-and-control (C&C) server attacks also grew 94% to 1,026 reported incidents last year. These were fuelled partly by the increase in such servers distributing the Emotet and Cobalt Strike malware, which accounted for one-third of malware in C&C servers.
Some 6,600 botnet drones with Singapore IP addresses were identified daily last year, up from 2,300 in 2019. CSA revealed that Mirai and Gamarue malware variants were prevalent amongst infected botnets in 2020, with the former malware targeting primarily Internet of Things (IoT) devices.
But while COVID-19 themed phishing campaigns were pervasive globally, Singapore-hosted phishing URLs dipped 1% to some 47,000 last year. Defacements affecting “.sg” website also fell 43% to 495 cases last year, with SMBs again mostly impacted by such attacks. CSA said this dip might be due to activist groups opting to target other platforms such as social media to drive awareness of their causes.
In total, 16,117 cybercrime cases were reported last year, accounting for 43% of all crimes in Singapore. The number also climbed from 9,349 cases in 2019.
Online scams were the most common form of cybercrime in the city-state, with such cases up 62% to hit 12,251 last year, compared to 7,580 in 2019. CSA noted that the this was due to the accelerated growth of e-commerce as well as community marketplace and social media platforms, as more users in Singapore turned to online shopping amidst the global pandemic.
CSA said: “Throughout 2020, global threat actors had capitalised on the anxiety and fear wrought by the pandemic, with repercussions felt by individuals and businesses. These threat actors made their presence felt, targeting areas such as e-commerce, data security, vaccine-related research and operations, as well as contact tracing operations.
“Some of these trends were mirrored locally, where a surge in ransomware incidents as well as the emergence of COVID-19-related phishing activities were seen. These also coincided with the rise of work-from-home arrangements, as individuals and businesses adopted new technologies to maintain business continuity,” the government agency said.
It pointed to an increasingly complex security landscape, where it anticipated ransomware to evolve into “a massive and systemic threat”. Such attacks were no longer confined to sporadic and isolated incidents, it warned, noting that the recent spate of high-profile ransomware attacks worldwide had affected critical service providers and major organisations, including Colonial Pipeline and JBS.
These incidents indicated that cyber attacks could have real-world effects and had the potential to become national security concerns, CSA said. It urged organisations to assess their cybersecurity readiness and ensure their systems were sufficiently resilient to recover from such attacks.
It also warned that cybercriminals would increasingly target remote workers, given the rise of such work arrangements amidst the COVID-19 pandemic. “Poorly configured network and software systems, which are part of the new remote work ecosystems, have widened the attack surface and exposed organisations to greater risk of cyber attacks,” CSA said.
Supply chains also were expected to be targeted and attacks more sophisticated, it said, pointing to the SolarWinds breach.
CSA’s chief executive and commissioner of cybersecurity David Koh said in the report: “Cybersecurity threats to supply chains have been around for more than a decade, but the impact of the SolarWinds attack was unprecedented. The incident is a stark reminder of the cybersecurity risks that all companies–big and small–face within their supply chains and when engaging third-party vendors, which is a near-certainty in today’s highly-interconnected global economy.
He added that ransomware had transformed from “a sporadic nuisance” impacting just a handful of machines to a massive threat affecting entire networks of large enterprises. “This is now a major security issue that affects critical information infrastructure (CII) sectors and nations,” Koh said.
RELATED COVERAGE
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.

