Used routers are leaking sensitive data. Don’t make the same mistake with your PC
A report from ESET this week highlighted a surprising fact: Businesses selling old network equipment sometimes fail to wipe them of private data, leaving corporate IT secrets out and open in the wild.
The findings reveal that of the 18 secondhand routers purchased by ESET researchers, half had been left exactly as when in use. Only five had gotten fully scrubbed of information about the network, credentials, and even physical building security. From the available data, hackers could glean usernames, password hashes, and other details useful for engineering an attack on the business. And the issue comes up repeatedly, as Ars Technica notes in its coverage of ESET’s investigation.
This discovery might sound far removed from your life as an individual, but the lesson—and the warning—in this reveal is highly relevant. If you don’t wipe your own devices before selling or recycling them (yes, including your home router), you’re leaving yourself vulnerable to malicious actors.
Your PC is a primary example. Its storage drive(s) likely hold scads of sensitive data. Taxes, personal hobbies, budgets—the full spectrum of your life touches your computer. Just imagine if a malicious actor got hold of your old hard drive, where you left a plain text document with all your passwords on your desktop. At that point, it’s sadly too late to wish you’d been using a password manager, which would have protected against that kind of accidental access to your credentials. And the fallout could be incredibly damaging—financially at the worst, but at minimum your schedule and peace of mind will take a hit as you address the issue. So when it comes time to part ways with your PC, smartphone, or other tech gear, you should nuke the data on them properly.
PCWorld
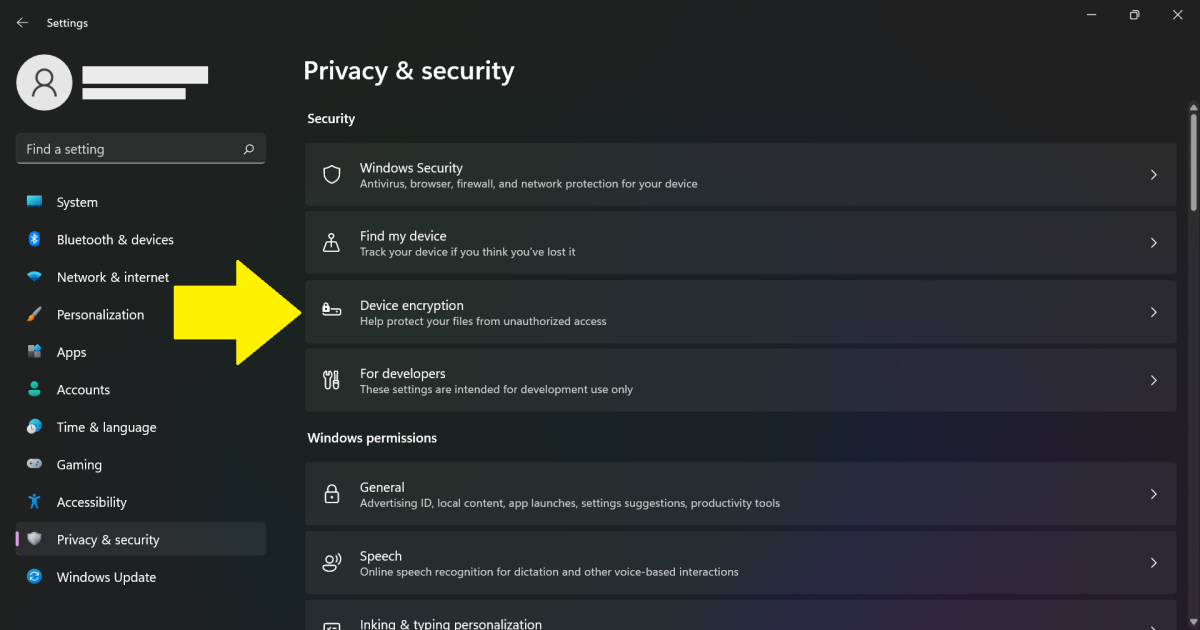
You can actually take a preemptive step toward that goal now, by encrypting your devices (as applicable). Without the decryption key, the data is scrambled and unusable, and if the drive is then wiped, retrieving the data with the key afterward becomes difficult. To encrypt your PC, you can use one of these two methods:
- Most users with a Windows Home license will have Windows device encryption activated if you sign into your computer with a Microsoft account.
- Windows Pro users can opt instead for BitLocker, which offers more flexibility in management of the encryption.
The caveat about encryption, of course, is that what locks out others can lock you out, too. You should maintain backup access to your decryption key, whether that’s BitLocker’s recovery key or ensuring you’ll always have access to the Microsoft account controlling your Windows device encryption.
As for the actual wiping of your PC, you have a couple of options. Combined with device encryption, both methods become even more effective:
- Faster, but less secure: When using Windows’ reset option, choose the version that also cleans the drive. However, while this action makes recovering data harder, it’s still possible.
- More secure: Our guide to securely erasing your drive explains how to use software like Eraser (for hard disk drives) and commands like Secure Erase (for SSDs) to thoroughly and properly remove all traces of your data.
What about smartphones? They follow a similar process, though even more simplified. Most have encryption on by default, making their basic reset option acceptable.
You may not have the resources of a corporate IT department, but you don’t need to protect yourself better that one. As this research into business practices show, companies don’t always follow the proper procedures. Be smarter than them and do things the right way.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.

